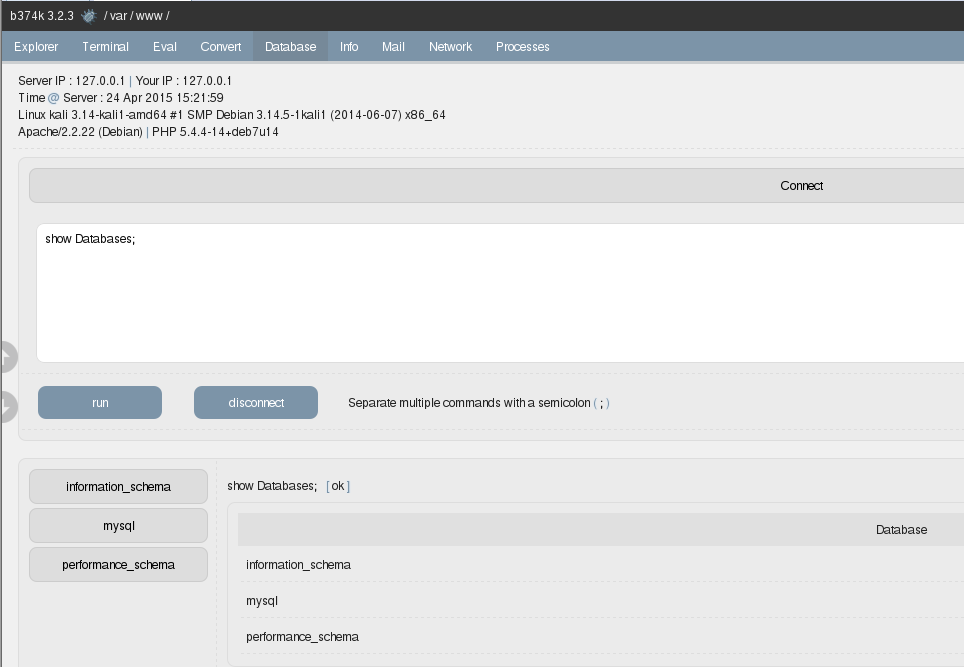
While performing a web application penetration testing, at times you are able to find out the web application is running MySQL database through “root” credentials. This is one of the biggest NO of security. In this case, we can get a root shell on the machine with just a few commands. Here comes my second cheat sheet so that I do not forget this anymore.